things turning me on this week
☕enjoy with a hot cupa java/script
k3s from Rancher
I’ve been using kubeadm, professionally, for a few years now.
It’s been very good. At Internet Archive, we run everything “on-premise”.
So using AMZN S3, Google GKE, Azure or similar, are out for us.
After a few “perfect storm” of issues in the last 90 days, I started researching on the web, and in devops Slack communities of 15k to 100k engineers, I started looking into k3s.
The current conventional wisdom on k3s from Rancher Labs is that it’s small, lightweight, and great/ideal for devices with minimal RAM/CPU, “Internet of Things”, raspberry PIs, and more.
However, I’m here to tell you, it seems fantastic for more than just that.
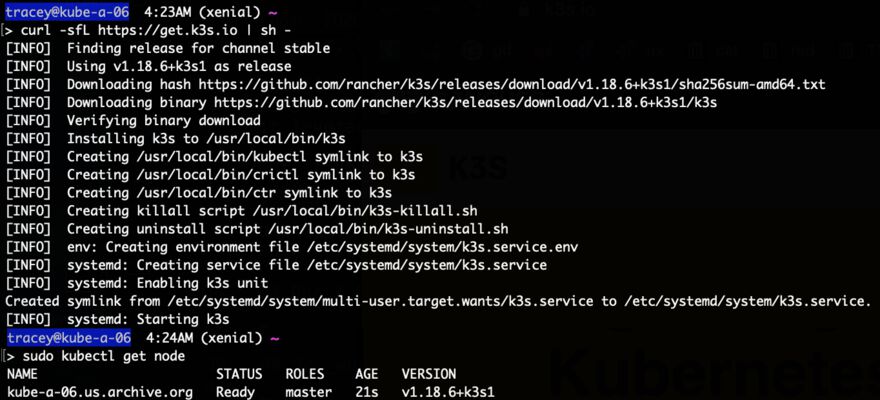
k3s, not unlike nomad, plays a very cute trick. In it’s “one-shot” installer:
curl -sfL https://get.k3s.io | sh -
– which indeed will be up in seconds, it leverages a single (presently ~50MB) binary single executable (to /usr/local/bin/k3s)
But it doesn’t end there. Going with their wonderful “one shot” installer vibe, you don’t need docker installed, or kubectl. They simply symlink kubectl to their binary (and implement full CNCF verified compatibility) and implement crictl API for docker building and deployment. All with one binary! (And they also auto-detect and systemd setup a daemon to auto-restart on reboot, etc.)
Don’t Blink
It comes up so fast and ready to go, it’s a bit hard to believe! Give it a try on a virtual machine you have access to. They have a single “uninstall and remove all traces” script they print out during the install that … you guessed it, takes only seconds to run.
So what’s the catch?
There isn’t one, really. But I did find a few minor things I needed to do to “drop-in replace” with GitLab and their full “Auto DevOps” CI/CD pipelines (which we use extensively at my work).
Minor things:
- need to change GitLab’s annotation from default
nginx ingressto traefik loadbalancer - which is what comes withk3s - remove a GitLab default secret (for https) that doesn’t get used with
traefikand causes auto-https (viatraefikbuilt-in lets encrypt ) to fail - as of now there’s a “one-shot” issue with setting up the admin email address for the lets encrypt part of
traefik
Right, so….
I (continue to) keep archive.org’s
installers for kubernetes and nomad installers updated here via the kre8 and nomad repositories.
Here are my notes on GitLab + k3s + k8s full CI/CD:
Prerequisites:
ssh-able unix node you havesudoon- wildcard DNS pointer to the IP address of your 1st node. you can, alternatively, temporarily edit your laptop
/etc/hostsand point some nice internet public url hostnames to your 1st node IP address.
Helpful links/scripts I maintain actively:
- https://gitlab.com/internetarchive/kre8 – repo and code used to create and interact with k3s-based kubernetes clusters
- https://gitlab.com/internetarchive/kre8/-/blob/master/README.md – notes on minor tweaks to
k3sinstaller for those interested in https/lets encrypt - https://gitlab.com/internetarchive/kre8/-/blob/master/k3s-ci.yml – CI/CD setup and tweaks (some required; some I prefer) to GitLab’s Auto DevOps
Give k3s a try!






Comments
tracey pooh
traefikfolks, over the weekend I updated the installer from v1.7 to v2.2+ (which is more flexible, but adds a bit more complexity to the setup for https)